Artificial Intelligence and Cybersecurity
Rapid Prototyping
Designated a Cyber AI/ML Center of Excellence, IntelliGenesis’ IG Labs™ Division creates advanced cyber and data science solutions while driving research and development, and rapid prototyping of entirely new capabilities that demonstrate “The Art of the Possible.” Developers working in our 8,000sqft state-of-the-art facility have the tools and freedom to create inspired applications and hardware solutions that solve complex problems and advance the mission in new ways.
- DGX A100 – Accelerated AI/ML training and development using the power of GPUs
- Cyber Ranges – Realistic system/network environments for cyber exercises and training
- KrakenAI™ – Conversational AI delivering cybersecurity focused decision-making support
- Microelectronics Fabrication – Design and prototyping resources for custom hardware and flyaway kits

Fabrication Lab

Cyber AI/ML Lab

Classroom
Our cutting-edge Artificial Intelligence Infrastructure, Rapid Prototyping Fabrication Lab, and Cyber-Physical technologies enable new approaches to old problems. After an initial solution is developed, we always follow up with the question, “What if we couldn’t do it that way?” which forces developers to change their thinking and come up with new ideas they wouldn’t normally consider. Often, parts of the secondary discussion are integrated with the initial solution to develop a comprehensive final design.
Our experts deliver forward-thinking, holistic products that advance our customers’ capabilities and enable defenders to stay ahead of adversaries’ technological advancements. IG Labs provides extensive resources and expertise in a hands-on environment to transform our customers and partners into next-generation influencers of change. IG Labs primarily focuses on two pillars—Artificial Intelligence and Cyber. We further break down our expertise into four cross-collaborative areas that influence and advance each other: Generative AI (GAI) and Large Language Models (LMM), AI/Deep Learning, Data Science/Advanced Analytics Development, and Defensive Cyber Solutions.
-

Generative AI & Large Language Models
Cognitive support solutions designed to empower operators with AI- enhanced decision-making ability. Bridging the gap between cyber operators and GAI while scaling to meet mission requirements and changing demands.
-

AI/Deep Learning
Leveraging the full spectrum of cutting-edge tools and methods, we provide solutions tailored specifically to the problems they are trying to solve. IG Labs solutions are also bolstered by our NVIDIA Deep Learning Pod to produce real mission outcomes.
-

Data Science/Advanced Analytics
We continuously create innovative analytics and data science capabilities that enable our customers to discover big data’s previously unrealized value.
-

Defensive Cyber Solutions
IG Labs is founded on gaining and maintaining the high ground. We defend against cyber threats that could threaten the daily lives of millions, even as they innovate and adopt more sophisticated tools and techniques in near-real-time.
-

“IG Labs is amazing. The ability to work hands on with open-source data sets and tools is really something that you don’t find easily.” -

“I have been impressed with the work and outcomes of the CYBERSPAN team, looking forward to seeing the next phase of this project success!”
Innovative Products
IG Labs offers a range of cybersecurity, training, AI/ML services and products to improve your cyber capabilities. We also offer customized solutions to meet your unique mission needs. Our products encapsulate our more than 16 years of Cyber and AI expertise in self-contained, repeatable ways so we can readily provide these bleeding-edge technologies and methodologies to enhance missions worldwide.
CYBERSPAN™
- Agentless Network Monitoring
- Analyzes Network Traffic
- API access to all data in JSON and STIX formats
- Maintains privacy of users
- Maintains privacy of user activity
- Monthly Updates
- Data Exfiltration
- Denial-of-Service Attacks
- Ransomware
- Port Knocking
- Non-standard Port Use
- Proxy Misuse
- ATT&CK Mitigations for Detected TTPs
- Data Volume Metrics
- Protocol Type Distribution
- Anomalous and Malicious Activity
- Packet: Analyzes all network traffic to detect and identify anomalous activity across the entire network
- Device: Detects anomalous activity in the context of a single device
- Time: Identifies time periods which contained anomalous activity on the network
- Maps malicious network traffic to known MITRE ATT&CK Tactics, Techniques, and Procedures (TTPs)
- Performs predictive analysis of traffic sizes to identify anomalous volumes
- Incorporates output of other Intrusion Detection Systems to strengthen analysis
- Examines the user agent string for consistency and accuracy across connections
- Installation Guide
- On-site Installation and Troubleshooting Support
*Available for Additional Cost
- On-site Installation and Troubleshooting Support
- Other Data Processing
- Other Analytics
- Other Data Models
- CYBERSPAN™
- Request Pricing and Additional Information
M.A.C.E. System
Provides practical OT and IT Cyber Physical training in a mobile converged environment with real-world hardware and protocols
- Plug-and-Play Components
- Real-World Protocols
- Modular Design
- Vendor-Agnostic
- Converged OT and IT Environments
- Cyber Range Integrations
- Easy Transportation/Set-up
- Hands on Critical Infrastructure Cybersecurity
- Build skills and knowledge to include Logic Controllers, Control Systems, Communication Technologies, Sensors, OSINT, Vulnerability Assessments, Penetration Testing, and Integrated Defense Controls
- Obtain experience in operational technology
- Gain an edge against adversaries and cyber threats
- Gain insight and real-world experience in critical infrastructure and OT life-cycle
- Laptop with minimum specs below:
- Intel Core i5 (64-bit)
- Intel HD Graphics 4600 Graphics Card
- 8 GB RAM (DDR3L)
- 10/100/1000 Mb/s Ethernet (RJ-45) Wired Network Connection
- 1 HDMI
- 1 Mini DisplayPort
- USB 3.0 (x2)
- Maximum Resolution: 1366 x 768
- COTS Single Board Computer
- Touch Display Screen
- Sensor Modules
- Hardware Module
- Ruggedized Case
- Course Material
- New Course Modules included for one year after initial purchase
*Available for Additional Cost
- Additional Training Modules
- Annual Subscription to Module Updates
- Customized Modules Developed by Request
- M.A.C.E. System
- Request Pricing and Additional Information
NeuralNexus™ – Machine Learning as a Service (MLaaS)
Unleashing the power of interconnected intelligence
- Intuitive Dashboards for Security Management
- Customizable Threat and Vulnerability Use Cases
- Smart Sensor Integration for Advanced Defense
- Designed for AI/ML Threat Detection and Mitigation
- Universal Data Compatibility
- Generative Capabilities for Threat Simulation
- Collaborative Platform for Team-based Security Management
Multi-User Platform
- Active Prediction Pipelines
- Dynamic Static Analysis
- Real Time Data Management
- Financial Services
- Healthcare
- Public Sector
- Transportation
Cyber Use
- Dynamic Threat Detection
- Real-Time Threat Detection
- User Behavior Analysis
- Vulnerability Assessment and Remediation
- Security Event Correlation and Analysis
- Fraud Detection
Recommended Requirements:
For a small to medium-sized business*
- CPU: At least 4 cores (preferably 6 or more)
- GPU: A more powerful NVIDIA GPU, such as the one in Jetson Xavier NX or
AGX Xavier - RAM: At least 16 GB, ideally 32 GB or more
- Java 8 or Java 11
*These upgraded specifications will enable superior performance and handling of network traffic in a business environment with comprehensive security needs. Additional factors, like the complexity of your defense models and the volume of data being processed, may also affect system performance.
- Flexible to Security Demands of Various Sizes of Businesses
- Easily Adaptable to Evolving Threat Landscapes
- Optimized for High-Volume Data Processing and Complex Security Environments
- NeuralNexus™
- Request Pricing and Additional Information
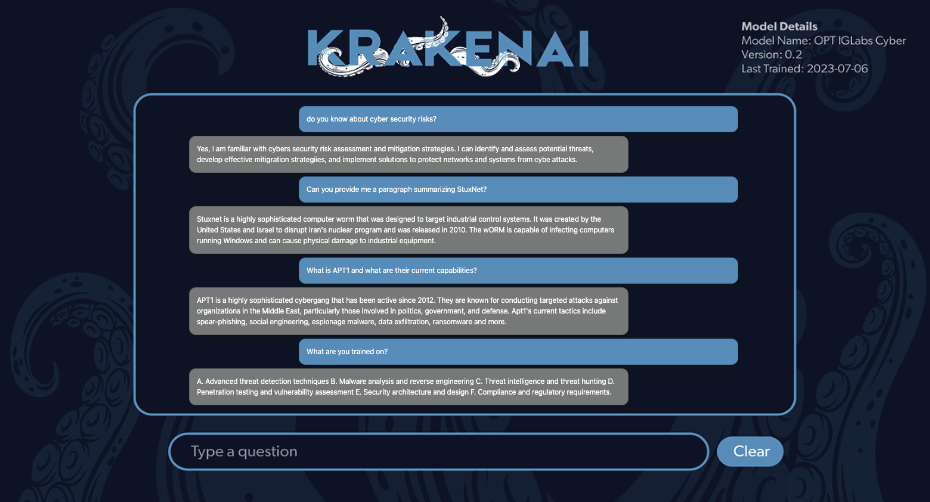
KrakenAI™
Generative AI for Cybersecurity Needs
- Distributed Computing: Enhanced speed and application efficiency
- Session Management: Secure, vast data storage and personalized user experience
- Data Persistence and Caching: Boosted application speed and groundwork for user-driven question analytics
- Advanced Text Generation Techniques: Enhanced result diversity and relevance
- Enumerate Network and Domain
- Identify potential vulnerabilities in network
- Mimic Threats
- Dark Web Threats
- Usernames Enumeration
- 8x NVIDIA A100 80B Tensor Core GPU’s
- 5 petaFLOPS AI
- 10 petaFLOPS INT8
- 2TB
- OS: 2×1.92TB M.2 NVME drive Internal Storage: 30TB (8×3.84TB) u.2 NVMe drives
- Flexible to demands of business size
- Easily integrates numerous cybersecurity tools
Past Performance
-

XXXXXX-XX-C-0350 (Prime)
Key Tasks: Analytic Platform Development; Predictive Analytics; Big Data AnalysisOn this contract, IntelliGenesis performed platform and analytics development for big data analysis to produce forensic models and predictive capabilities for threat actors’ cyberspace behaviors. Our developers applied data science techniques like clustering and collaborative filtering to identify Advanced Persistent Threats (APTs) and attribute their specific tactics, techniques, and procedures (TTPs), then make predictions as to what TTPs an APT may use next. IntelliGenesis designed and developed the full analytic platform including backbone analytics, user interface, and a custom Attacker Search database feature to help users like cyber operators immediately identify known attackers.
-

XXXXXX-XX-C-0006 (Prime)
Key Tasks: Analytic Platform Development; Predictive Analytics; Threat AttributionIntelliGenesis performed full-lifecycle development of an advanced analytic tool that conducts real-time network traffic analysis across the cyber infrastructure and provides alerts for anomalous or malicious activity. This tool incorporated a set of anomaly detection models that identify unusual network traffic without prior knowledge or training on a network’s normal activity. This tool eliminated the maintenance and upkeep associated with endpoint monitoring, detected anomalies in non-traditional network device traffic that cannot be monitored by endpoint software, and maintained user privacy by only analyzing their metadata.
Offices:Maryland Headquarters Georgia Office Texas Office |
Contact Info:Email: Identifiers:DUNS Number |
Locations:•Maryland |
|