Newsroom
News

IntelliGenesis Partners with TeamWorx Security
| Chris Sullins | Press
IntelliGenesis is excited to be part of Howard County’s transformation into Maryland’s newest tech hub. Our partnership with TeamWorx Security at the Maryland Innovation Center has been invaluable, allowing us to collaborate and expand our AI-powered …
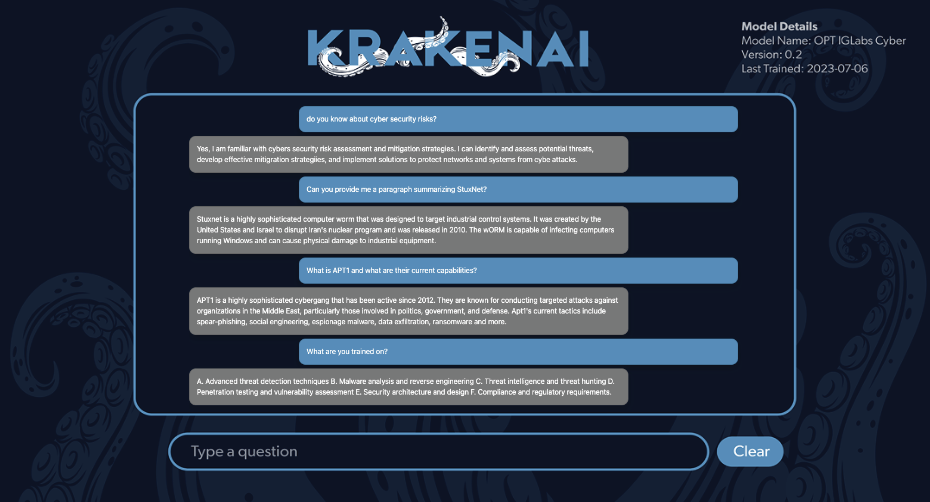
IntelliGenesis Unleashes KrakenAI™
| Angie Lienert | Press
KrakenAI™: A new Generative AI Tool to Augment Cyber Operations
IntelliGenesis LLC’s IG Labs Division announced today the launch of their newest capability, KrakenAI™, a cutting-edge generative artificial intelligence (AI) large langu…
IntelliGenesis LLC Unlocks the Potential of AI
| Angie Lienert | Press
NeuralNexus™ Becomes an AI/ML Success Story Unleashing Intelligence
COLUMBIA, MD. APRIL 19, 2023
Today, we stand on the precipice of a new era where AI-driven dataflows and generative capabilities unleash the potential of interconnected in…
Blog

Why Do So Many AI Projects Fail?
Written by Chris Sullins on . Posted in Blog.
What if you spent more than half a trillion dollars and got almost nothing in return? IDC estimates that by 2028, corporate spending on AI solutions will climb to $632 billion from just over $300 billion in 2025. Yet, despite this massive investm…

CYBERSPAN® Featured in I95 Business: Bringing Defense-Grade Cybersecurity to Small Businesses
Written by Chris Sullins on . Posted in Blog.
I95 Business profiled our CYBERSPAN® platform in its cybersecurity coverage this month as a new line of defense for the vulnerable small and mid-sized businesses that are increasingly targeted by sophisticated threats. The article discusses how we…

AI is a Power Tool, Not a Pink Slip
Written by Chris Sullins on . Posted in Blog.
Progress tends to make people uneasy and is often met with resistance. Even something as seemingly innocuous as the introduction of writing more than 5,000 years ago drew criticism that it would diminish memory and other cognitive abilities. At the tim…
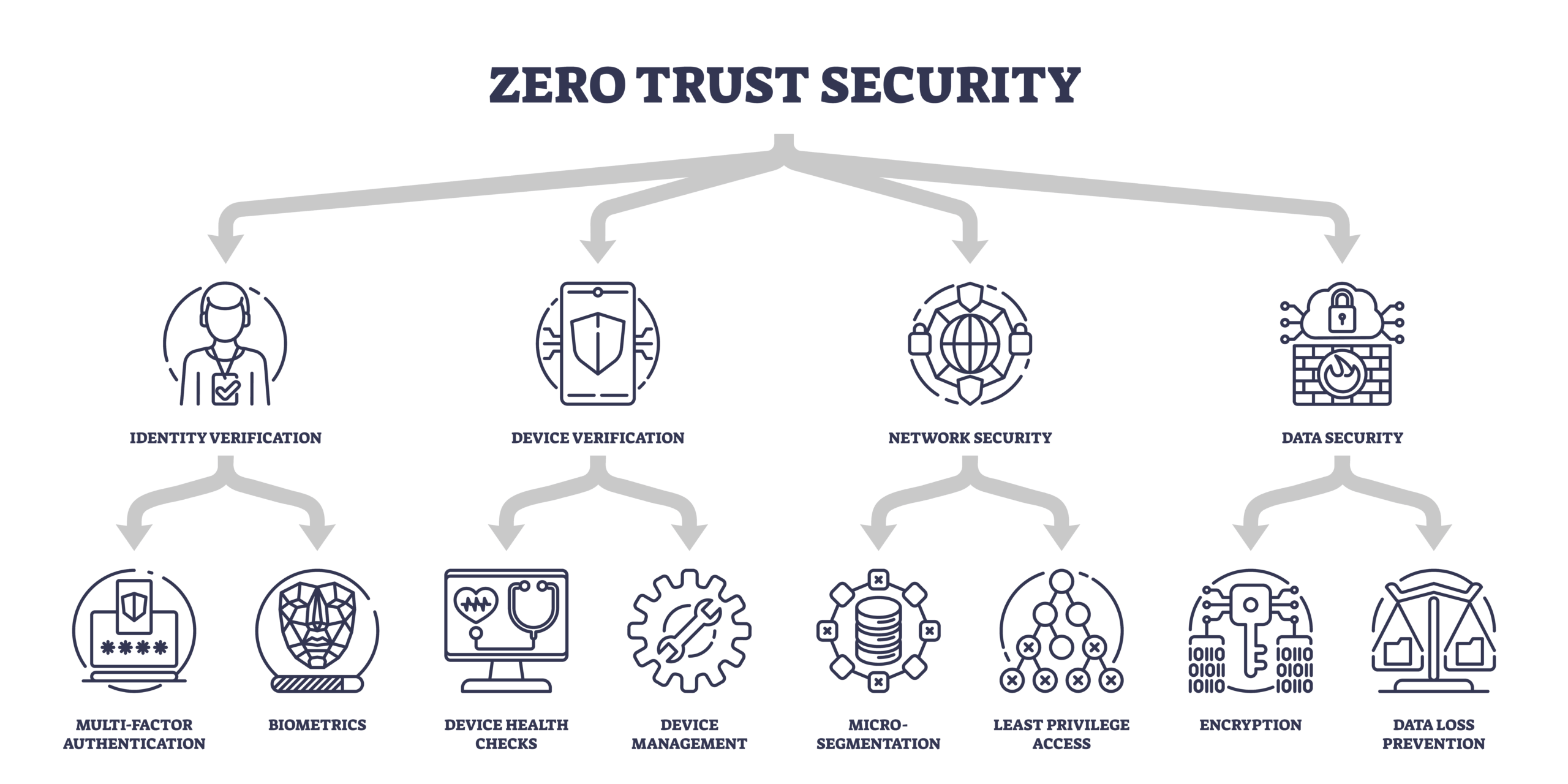
Why Network Detection & Response is a Key Component of Zero Trust Architecture
Written by Chris Sullins on . Posted in Blog.
Zero Trust is a straightforward concept: never trust, always verify. With the June 2025 release of NIST SP 1800-35 from the National Institute of Standards and Technology (NIST), Zero Trust is back in the cybersecurity spotlight. But now the focus has …

The MITRE ATT&CK® Framework: It’s More Than TTPs
Written by Chris Sullins on . Posted in Blog.
When most cybersecurity professionals think of the MITRE ATT&CK® framework, they think of TTPs—tactics, techniques, and procedures. These terms have become shorthand for how attackers operate and are often used to guide detection and response strat…

Understanding North-South vs East-West Network Traffic
Written by Chris Sullins on . Posted in Blog.
Why It Matters in Securing Your Network
Not all network traffic is the same. Depending on where it’s headed and where it came from, network traffic can behave differently and pose different security challenges. Some threats come from the outside or…