
The MITRE ATT&CK® Framework: It’s More Than TTPs
When most cybersecurity professionals think of the MITRE ATT&CK® framework, they think of TTPs—tactics, techniques, and procedures. These terms have become shorthand for how attackers operate and are often used to guide detection and response strategies. But ATT&CK is more than just a static list of hacker moves. The framework is structured around interconnected building blocks known as objects that describe adversary behaviors, tools, mitigations, and other elements. More importantly, these objects have meaningful relationships between them, which turns ATT&CK into a dynamic, contextual map of the threat landscape.
Beyond Tactics and Techniques: The Objects of ATT&CK
ATT&CK objects—such as techniques, groups, software, and mitigations—aren’t just categories; they’re uniquely defined entities with consistent names and IDs. These are what people refer to when discussing attacker behaviors and defensive strategies, like T1189: Drive-by Compromise and M1021: Restrict Web-Based Content. This shared vocabulary allows both human analysts and automated security tools to describe and understand threats in a consistent way.
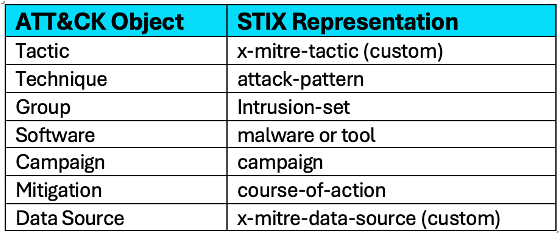
To make this vocabulary usable across platforms and products, ATT&CK data is formatted using STIX 2.1. STIX (Structured Threat Information Expression) is a standardized format for structuring cyber threat intelligence in a machine-readable way so tools and security teams can work from the same threat model. Here’s a quick review of the main ATT&CK objects and their corresponding STIX object types:
- Tactics: Tactics represent the goal the attacker is trying to achieve at each stage of an attack. In STIX, the unique ATT&CK tactics use a custom type: x-mitre-tactic.
- Techniques: Techniques describe the specific methods used to accomplish a tactic. Many techniques are broken down further into sub-techniques. This component also provides detection references for this kind of attack. Both are modeled as attack-pattern objects in STIX.
- Groups: Groups are specific threat actors that have been identified and tracked, such as Advanced Persistent Threats (APTs) or cybercriminal organizations. In STIX, these are represented as intrusion-set objects.
- Campaigns: Campaigns are real-world attack operations across a defined period of time. Campaigns are represented in STIX as campaign objects.
- Software: Software includes both malware and legitimate tools repurposed for malicious use. In STIX, software is represented as either malware or tool objects.
- Mitigations: Mitigations provide defensive recommendations to reduce or limit the impact of a technique or software. These map to the STIX course-of-action object.
- Data Sources: Data sources identify where evidence of an adversary’s activity might be found, such as log files. Like tactics, data sources are modeled in STIX using a custom object type: x-mitre-data-source.
STIX not only defines how objects are formatted, but also how they relate to one another, and how they can be queried by cybersecurity tools. Each ATT&CK object implemented in STIX has consistent properties, globally unique identifiers, and most importantly, relationships. This allows disparate security tools to refer to the same thing unambiguously. Without STIX, each vendor or analyst would need to define these relationships themselves, which undermines the consistency and interoperability that makes ATT&CK so useful in the first place.
Connecting the Dots: Relationships That Empower Defense
Understanding ATT&CK’s individual object types is only half the story. The real power of ATT&CK is in the relationships between these objects.
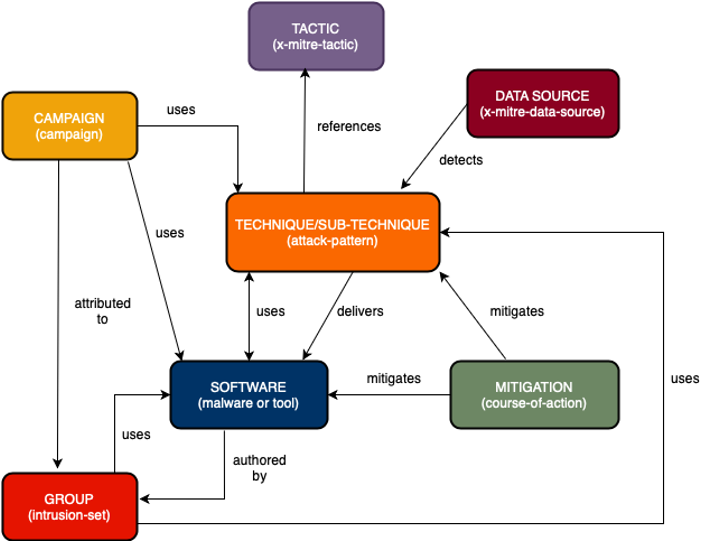
Techniques are connected to the tactics they serve, the software that enables them, the groups and campaigns that use them, and the data sources that detect them. Similarly, groups are linked to the software and techniques they rely on, while mitigations tie back to the techniques and malware/tools they’re meant to stop. These STIX-defined relationships turn ATT&CK into a map of adversary behavior that helps defenders piece together what an attacker is doing, how they’re doing it, and how best to respond. The following diagram illustrates how these ATT&CK objects interconnect.
These interconnections are what enable mapping one indicator or TTP to an ecosystem of related knowledge. Instead of responding to one-off alerts, analysts can understand how different pieces of an intrusion tie together. When an incident breaks out, a defender can more quickly answer: What kind of attack is this? Who might be behind it? What might they do next? How do we stop it?
CYBERSPAN®: Putting ATT&CK Relationships to Work
As an AI-driven network detection and response (NDR) solution, CYBERSPAN® demonstrates what’s possible when a security tool fully embraces the MITRE ATT&CK framework, not just its TTPs.
What does this look like in action? CYBERSPAN® continuously monitors network traffic and uses machine learning to spot unusual patterns that could indicate malicious activity. When it finds something odd, CYBERSPAN® maps the behavior to MITRE ATT&CK tactics and techniques to see if it matches any known threat patterns. Alerts come with plain-language explanations and direct references to ATT&CK, so defenders have insight into what’s happening and why it matters.
From there, CYBERSPAN® references ATT&CK’s structured relationships. It automatically identifies any associated threat groups, commonly used software, and the corresponding mitigations to the detected technique. This context allows analysts to also see how the initial malicious activity fits into the broader adversary playbook. In effect, CYBERSPAN® is saying, “We’ve seen something like this before in known attacks and here’s what typically comes next.”
CYBERSPAN® then uses these connections to recommend immediate defensive action. In fact, CYBERSPAN® automatically pulls in the MITRE mitigations associated with any detected threat, presenting them on the dashboard. ATT&CK’s relationship structure also allows CYBERSPAN® to anticipate what threat activity might come next and recommend proactive measures. In other words, “Threat actors who behave like this often do these other things, and here’s how to prepare.”
The framework’s relationships also allow CYBERSPAN® to prioritize alerts more intelligently. If a detected technique maps to a critical tactic like Exfiltration, it can raise the priority of that alert. Similarly, if an event is linked to a known threat group given the techniques or tools that a group typically uses, the system can flag it as higher risk.
In short, CYBERSPAN® shows what’s possible when a security tool doesn’t just reference ATT&CK TTPs but fully integrates the object relationships that make ATT&CK so powerful. By using ATT&CK as more than a checklist, CYBERSPAN® helps defenders understand who might be attacking, what they’re trying to do, how they’re doing it, what’s coming next, and how to stop it.