
The Power of Predictive Analytics in Cybersecurity
In cybersecurity, reacting quickly is good, but anticipating what’s coming next is even better.
What are Predictive Analytics?
Predictive analytics combine network data and threat intelligence with machine learning techniques and natural language processing to anticipate an attacker’s next moves.
How does it work? Algorithms analyze mountains of data—network traffic, login patterns, file sizes, IP addresses, and more. If something unusual occurs, predictive models flag the activity as suspicious.
But these models don’t just tell you what’s happening now, they tell you what will likely happen next. Attackers don’t break into a network and immediately begin stealing data. Instead, they typically follow a recognizable sequence of behaviors before reaching their final objective.
For example, if a user who never runs PowerShell starts executing a script, gathers login credentials, and accesses machines they don’t typically use, predictive analytics can link these behaviors and recognize them as the early stages of a potential data exfiltration attack. Next steps will likely involve data collection, connecting to an external system, and stealing data.
By identifying these early stages of an attack, predictive analytics give security teams time to proactively disrupt the likely next steps based on known adversary behaviors.
The MITRE ATT&CK® Framework: The Gold Standard of Known Adversary Behaviors
To effectively predict threats, models rely on structured frameworks to understand adversary behavior. One of the most trusted is the MITRE ATT&CK framework—a comprehensive database of real-world tactics, techniques, and procedures (TTP) used by threat actors in actual cyberattacks. ATT&CK (Adversarial Tactics, Techniques, and Common Knowledge) provides clear descriptions of how attackers get into a network, move around, and achieve their goals.
This framework organizes cyber threats into a simple structure:
- Tactics describe the goals attackers have when launching attacks, such as gaining Initial Access.
- Techniques describe how attackers achieve these goals. Phishing is a common technique.
- Sub-techniques break down the specific ways these techniques are implemented, such as using a Spearphishing Link.
- Procedures document real-world examples of how attackers have used these techniques. For example, APT32 has sent spearphishing emails containing malicious links.
- Mitigations suggest ways to prevent these attacks. A mitigation strategy for phishing is Restricting Web-Based Content.
One particularly valuable aspect of the ATT&CK framework for predictive analytics is its ability to reveal associations among techniques within TTP chains. By analyzing how attackers typically combine different techniques, predictive models can anticipate an adversary’s next steps based on techniques that have already been observed.
How CYBERSPAN® Anticipates Threats
CYBERSPAN®’s prediction engine works by correlating observed network behaviors with known adversary patterns. As it monitors network traffic, CYBERSPAN® flags any anomalous activity and then links each suspicious event to the MITRE ATT&CK framework.
This predictive capability is based on known APT (Advanced Persistent Threat) behavioral patterns from the ATT&CK framework. When CYBERSPAN® detects known TTPs, it identifies which threat actors commonly use these methods and what additional steps these actors typically take in their attack chains. This provides an early warning to defenders to help prioritize security responses.
To improve predictions, CYBERSPAN® enriches each event with additional data from other threat intelligence feeds. This includes known indicators of compromise—like IP addresses associated with botnets or phishing campaigns—as well as data from global internet scans. If your systems are interacting with known malicious infrastructure, CYBERSPAN® incorporates that into its analysis.
This correlation-based approach advances detection from isolated alerts to a bigger-picture view. By interpreting events as part of a potential attack path, CYBERSPAN® turns a flood of alerts into something manageable and actionable.
CYBERSPAN®’s Event Predictions
CYBERSPAN® communicates its predictive capability through its Event Predictions card, which displays a list of potential future threats based on recently observed activity. Each prediction links directly to its related MITRE ATT&CK page, giving security teams immediate access to detailed information about the predicted threat.
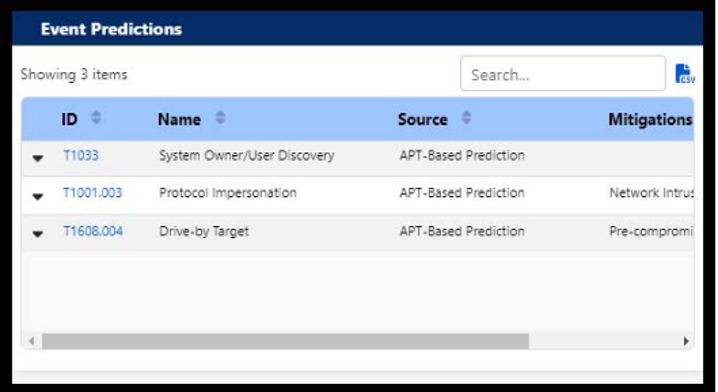
CYBERSPAN® Event Predictions Screenshot
Returning to our earlier scenario of a user running a suspicious PowerShell script, stealing passwords, and logging into other machines on the network. If the affected system then begins communicating with an unfamiliar external IP address over a non-standard port or starts sending unusual encrypted traffic, CYBERSPAN® may flag this as preparation for protocol impersonation. Protocol impersonation allows attackers to disguise their malicious activity as normal web traffic to avoid detection.
Additionally, CYBERSPAN® can recognize that these behaviors are consistent with attack patterns observed from threat groups like APT41, which are known to use PowerShell scripts, credential theft, lateral movement, and protocol impersonation to quietly expand access and exfiltrate data while avoiding detection.
Beyond Individual Networks: Community Intelligence
What makes CYBERSPAN®’s predictive capabilities even more powerful is its community-based approach to threat intelligence. The system aggregates anonymized data across its entire install base to identify broader patterns and emerging threats within specific industry sectors.
This community-based intelligence uncovers patterns that might not be visible when looking at a single organization, which further enhances CYBERSPAN®’s predictive accuracy.
Predict the Threat, Beat the Attack
Ultimately, predictive analytics provide something invaluable: time to prepare.
By combining comprehensive threat intelligence with predictive capabilities, CYBERSPAN® enables organizations to move from reactive security postures to proactive threat prevention. For businesses without extensive cybersecurity resources, this predictive edge is a huge advantage.